Security
Managed Defense That Makes Sense
A fully Managed Detection and Response service, combining security professionals and cutting-edge threat detection tools to safeguard your endpoints, networks, clouds, identities, and SaaS applications.
























Sofecta Labs provides
effective cybersecurity
with expert proficiency to secure your organization
Why Sofecta Labs
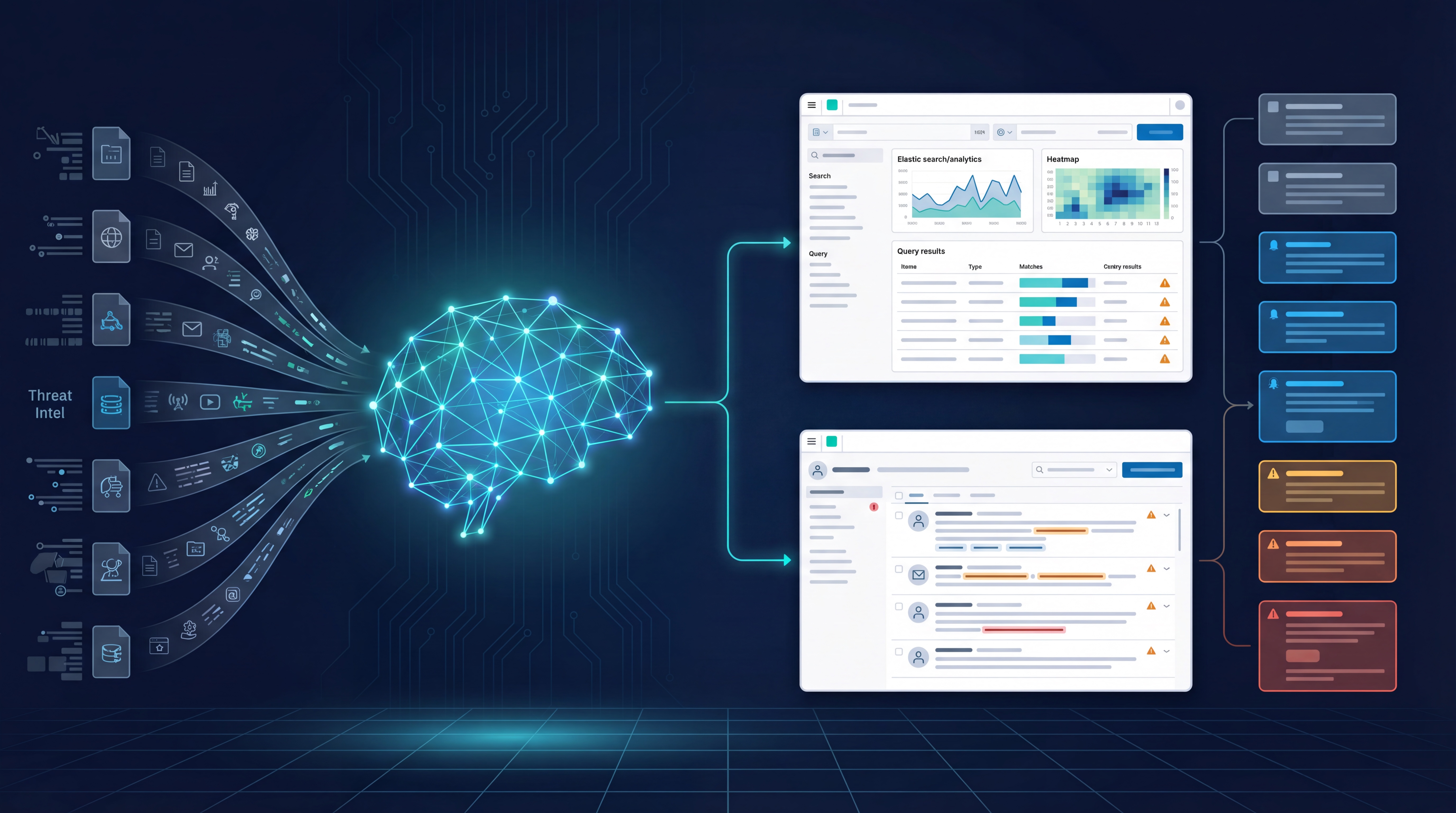
Sofecta Labs was created by merging Sofecta's XDR services and Deductive Labs' cybersecurity expertise. We pride ourselves on providing robust tools and technologies to detect and respond to advanced threats, such as malware, phishing attacks, and ransomware. Our solutions are customized to meet the specific needs and requirements of each customer, rather than using a one-size-fits-all approach.
Our core service is proactive MDR, which monitors network and system activity to detect any suspicious behavior and respond quickly to potential threats. We also have a strong understanding of data protection regulations and compliance requirements, offering security and compliance management services.
Our core service is proactive MDR, which monitors network and system activity to detect any suspicious behavior and respond quickly to potential threats. We also have a strong understanding of data protection regulations and compliance requirements, offering security and compliance management services.
End-to-end Security Solutions
Sofecta Labs offers comprehensive turn-key solutions with a variety of service options, including the integration of existing detection or IDS tools as part of MDR. Our extensive industry expertise and transparent service model guide our approach to designing and implementing security measures that align with your business operations, regulatory compliance, and risk profile.
Outcomes Oriented
Sofecta Labs primary focus is on delivering tangible security outcomes that directly contribute to the safety and resilience of your business. Our approach is proactive and risk-based, aiming to protect critical assets and enable your organization to continue its operations even in the face of cyber threats. Our goal is to bring measurable improvements to your cybersecurity posture and strategies that align with your business goals.
Expert Profiency
With strong hands-on experience in IT, software, and cybersecurity, Sofecta Labs encompasses a profound understanding of cybersecurity technologies and practices, along with the ability to adapt security stack and respond to evolving threats and risks. This ensures a high return on security investment and delivers unparalleled value to our customers.
Transparency and trusted
Cybersecurity is a co-operation with customers. Our principles of openness, honesty, and reliability in operations means providing clear and accurate information about security practices, policies, and measures to our customers. This transparency builds trust between Sofecta Labs and Customers, ensuring effective collaboration and adherence to ethical standards in safeguarding against cyber threats.
Explore industry-agnostic managed services
Managed Detection and Response combined with a multilayered security stack
Customize your cybersecurity and observability services by leveraging our Managed Service offerings. Select the appropriate monitoring assets for your business, and we will handle the rest. Enhance your existing security investments with our MDR and related services to elevate your security to an enterprise level. Or maybe you would like to unlock the possibilities of real-time Managed Observability features?
Our Solution
THREAT HUNTING
Identity protection
REsponse
investigation
AI-empowered SOAR assists enriching alert data, run parallel investigation and run autonomous response actions
Security expert-lead SOC provides deeperanalysis, reviews, and remediation plans for you
THREAT INtelligence
vulnerability management
Detection
correlation
XDR Analytics through hundreds of built-in correlation and ML rules
Built-in data normalization and long-term retention
Endpoints
Autonomous Protection
Vulnerability Protection
Threat Hunting
Networks
Vulnerability Protection
Threat Hunting
Cloud
Autonomous Protection
Threat Hunting
Identity
Autonomous Protection
Threat Hunting
Mobile Endpoints
Autonomous Protection
Vulnerability Protection
Threat Hunting
Email Exchange
Autonomous Protection
Threat Hunting
App Security
Vulnerability Protection
Threat Hunting
THREAT HUNTING
Identity protection
REsponse
investigation
AI-empowered SOAR assists enrichingalert data, run parallel investigationand run autonomous response actions
Security expert-lead SOC provides deeperanalysis, reviews, and remediationplans for you
Endpoints
Networks
Cloud
Identity
Mobile Endpoints
Email Exchange
App Security
Soon available for all MDR customers
ThreatCTRL - your asset and security management portal
We offer an easy-access approach to maintain your detailed asset inventory by combining security information, access rights, policies, and vulnerability statuses. Through the portal, you can also manage your fleet, services, and reports.

Asset management
ThreatCTRL offers a comprehensive list of all hardware, software, and network devices within an organization. Unique identifiers can be assigned to each asset to facilitate tracking and differentiation. Real-time monitoring of assets helps detect unauthorized changes, anomalies, or potential security risks to ensure assets are secure, up-to-date, and operating effectively. ThreatCTRL's asset management system can be seamlessly integrated with other systems, including MDM, identity management, security tools, help desk software, and procurement systems.
Security posture
ThreatCTRL provides our customers with a way to interact with their security data and understand their security posture. Our portal gathers information on emerging threats, vulnerabilities, and attack techniques to proactively enhance security measures. It also conducts assessments to identify and remediate security vulnerabilities in systems, applications, and infrastructure, and shows how the team responds to security incidents and breaches in a timely and effective manner.

BLOG


.png)
.png)